What Project Managers Need to know about Cyber Security?

If a project manager decides to bring on some new changes like creating a new Customer Relationship Management system or wants to move its IT infrastructure to cloud, then of course the project management must be very constructive. However, along with an effective project management it is important that the cyber security should be equally potent which ensures that the organization is not exposed to any security threats. Since several years cyber security has been a major concern for many organizations globally. This is mainly because of the growing cyber-crimes and an invasion of complex and disastrous cyber security attacks. Hence, project managers need to be very vigilant about the various security threats and trends. Let’s take a quick look at the cyber security essentials that every PM needs to know.
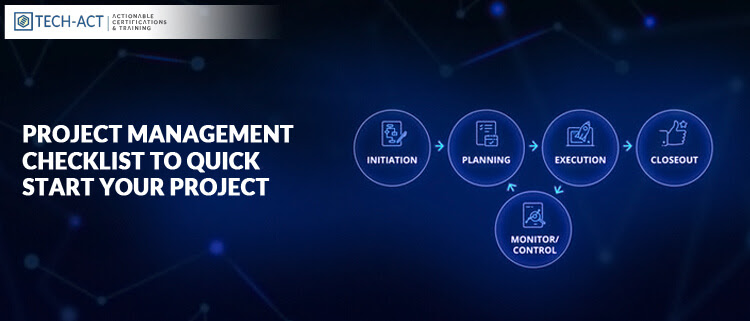
- Merge Security at Every Stage : There are various stages in project management that are listed below :
- Define the project requirements: The primary accountability of project manager is to meet the project objectives by managing & documenting client’s requirements and needs.
- Technical Stage: In this stage, the PM designs the entire framework of the project like determining the priority of the objectives and the total duration required to achieve each of them. Post which the project manager maps out the project execution plan.
- Management of Resource: In this stage, the PM evaluates whether the set objectives can be achieved with the available resources. This process consists of estimating the budget, management of team & time, assessing the risk.
- Final Stage: The outcome of the research are documented and presented which gives a clear picture of the estimated time & budget that would be required to achieve the desired goal.
In all the stages, security is very important. The above mentioned stages involve activities like collecting and storing sensitive data. Hence, if any of the information is leaked this would eventually build up a significant pressure on all the project management processes. Therefore, a project manager must ensure that all the essential security measures are taken prior initiating the first stage.
- Data Security is Crucial:Data security is a serious matter and yes it is an investment that will pay you in long run. We would recommend that PM should have a consulting with company’s financial expert to get an accurate understanding of ROI which would measure the success rate of implementing safe practices & also it is vital to a have a discussion with the IT development team as they can quickly give you an overview of the best practices that should be implemented for project security. It is important to determine all the possible channels through which the team’s sensitive data can be attacked. For instance, internet connection, voice calls, emails, messengers, file servers, website data, file transfers.
- Tighten the Security at Every Level: More focus should be placed on cyber security when it comes to IT or any technology based project. PM should assure that all the levels of corporate IT security are shielded to prevent any data breach. There are various levels of corporate IT security which are listed below:
- General Security: It consists of access management, registration safety, prevention from attack & fire safety.
- Infrastructure Security: It ensures protecting corporate devices, media files. It detects intrusions. In this, PM focuses more on prevention of the issues rather than dealing with the current issues.
- Communication Safety: It ensures that all the medium of communication are secure like email, voice call, instant messengers, and remote work.
- Wireless Security: Here, the PM ensures that all the wireless communication and file transfer which are used in the development process adheres with the best security practices.
- Cryptography: All the sensitive project data & confidential communication materials should be encrypted.
- Operational Safety: PM ensures that all the security guidelines and policies must be followed by the team.
- Assessment of Potential Risk: Nature of the project and the sources of exposure are the mains aspects which determine the level of risk. Let me explain you in detail.
- Nature of the project: Analyzing and calculating the amount of data which is stored in the organization’s server also understanding the type of data that is stored. For example, financial data, client data or internal company files etc…
- Sources of exposure: The higher the number of storage devices and online communication channels, the higher is the risk of data theft. However, this doesn’t mean you should keep all your eggs in one basket i.e. data centralization is not a solution rather it makes the work of cyber criminals easy. Hence, it is important to keep assessing the potential risk so that preventive measures can be taken and keep a regular eye on all the used data sources.
- Secure Communications: There are high chances of project data getting hacked when it is been transferred from one team member to another. Hence, communication protocols should be followed religiously to avoid such threats. It’s very important to understand what kind of files can be attached on emails & Skype and what kind of data should be transferred through secure encryption software. Popular tools for safe file transfer are pCloud Crypto, Enigmail, LastPass.
- Training to Employees: Project manager should make sure that all his team members are alert about the various security threats and also knows about managing the potentials risk. For this proper training should be imparted to the employees. For instances, Onboarding activities should include security training wherein the new employee is made aware of the best security practices and also gets trained on how to react to a situation if encountered with data breach. The new employees should also be updated on security policies which would teach them how to identify a potentially dangerous page.
Conclusion:
Cyber security has evolved a lot and will keep evolving in the coming times. Basic preventive measures like communication encryption and employee training are very effective practices for ensuring data security. So adapt a proactive approach for securing your valuable data rather than crying over the spilled milk later on.
All the best! Prepare well!
If a project manager decides to bring on some new changes like creating a new Customer Relationship Management system or wants to move its IT infrastructure to cloud, then of course the project management must be very constructive. However, along with an effective project management it is important that the cyber security should be equally potent which ensures that the organization is not exposed to any security threats. Since several years cyber security has been a major concern for many organizations globally. This is mainly because of the growing cyber-crimes and an invasion of complex and disastrous cyber security attacks. Hence, project managers need to be very vigilant about the various security threats and trends. Let’s take a quick look at the cyber security essentials that every PM needs to know.
- Merge Security at Every Stage : There are various stages in project management that are listed below :
- Define the project requirements: The primary accountability of project manager is to meet the project objectives by managing & documenting client’s requirements and needs.
- Technical Stage: In this stage, the PM designs the entire framework of the project like determining the priority of the objectives and the total duration required to achieve each of them. Post which the project manager maps out the project execution plan.
- Management of Resource: In this stage, the PM evaluates whether the set objectives can be achieved with the available resources. This process consists of estimating the budget, management of team & time, assessing the risk.
- Final Stage: The outcome of the research are documented and presented which gives a clear picture of the estimated time & budget that would be required to achieve the desired goal.
In all the stages, security is very important. The above mentioned stages involve activities like collecting and storing sensitive data. Hence, if any of the information is leaked this would eventually build up a significant pressure on all the project management processes. Therefore, a project manager must ensure that all the essential security measures are taken prior initiating the first stage.
- Data Security is Crucial:Data security is a serious matter and yes it is an investment that will pay you in long run. We would recommend that PM should have a consulting with company’s financial expert to get an accurate understanding of ROI which would measure the success rate of implementing safe practices & also it is vital to a have a discussion with the IT development team as they can quickly give you an overview of the best practices that should be implemented for project security. It is important to determine all the possible channels through which the team’s sensitive data can be attacked. For instance, internet connection, voice calls, emails, messengers, file servers, website data, file transfers.
- Tighten the Security at Every Level: More focus should be placed on cyber security when it comes to IT or any technology based project. PM should assure that all the levels of corporate IT security are shielded to prevent any data breach. There are various levels of corporate IT security which are listed below:
- General Security: It consists of access management, registration safety, prevention from attack & fire safety.
- Infrastructure Security: It ensures protecting corporate devices, media files. It detects intrusions. In this, PM focuses more on prevention of the issues rather than dealing with the current issues.
- Communication Safety: It ensures that all the medium of communication are secure like email, voice call, instant messengers, and remote work.
- Wireless Security: Here, the PM ensures that all the wireless communication and file transfer which are used in the development process adheres with the best security practices.
- Cryptography: All the sensitive project data & confidential communication materials should be encrypted.
- Operational Safety: PM ensures that all the security guidelines and policies must be followed by the team.
- Assessment of Potential Risk: Nature of the project and the sources of exposure are the mains aspects which determine the level of risk. Let me explain you in detail.
- Nature of the project: Analyzing and calculating the amount of data which is stored in the organization’s server also understanding the type of data that is stored. For example, financial data, client data or internal company files etc…
- Sources of exposure: The higher the number of storage devices and online communication channels, the higher is the risk of data theft. However, this doesn’t mean you should keep all your eggs in one basket i.e. data centralization is not a solution rather it makes the work of cyber criminals easy. Hence, it is important to keep assessing the potential risk so that preventive measures can be taken and keep a regular eye on all the used data sources.
- Secure Communications: There are high chances of project data getting hacked when it is been transferred from one team member to another. Hence, communication protocols should be followed religiously to avoid such threats. It’s very important to understand what kind of files can be attached on emails & Skype and what kind of data should be transferred through secure encryption software. Popular tools for safe file transfer are pCloud Crypto, Enigmail, LastPass.
- Training to Employees: Project manager should make sure that all his team members are alert about the various security threats and also knows about managing the potentials risk. For this proper training should be imparted to the employees. For instances, Onboarding activities should include security training wherein the new employee is made aware of the best security practices and also gets trained on how to react to a situation if encountered with data breach. The new employees should also be updated on security policies which would teach them how to identify a potentially dangerous page.
Conclusion:
Cyber security has evolved a lot and will keep evolving in the coming times. Basic preventive measures like communication encryption and employee training are very effective practices for ensuring data security. So adapt a proactive approach for securing your valuable data rather than crying over the spilled milk later on.
All the best! Prepare well!